The Open Web Application Security Project (OWASP)
OWASP is a non-profit organization dedicated to improving the security of software applications. It is an international organization that provides free resources and tools to help individuals and organizations understand and prevent software vulnerabilities.
Founded in 2001, OWASP has since become a leading authority in application security. The organization is run by a group of volunteers who are passionate about promoting the importance of application security.
OWASP has developed numerous resources that are freely available to the public, including educational materials, testing guides, and security tools. One of the most well-known resources provided by OWASP is the OWASP Top 10, a list of the most critical web application security risks.
The organization also holds numerous conferences and training events around the world, bringing together security professionals, software developers, and other stakeholders to share knowledge and best practices.
OWASP’s mission is to make application security “visible, so that individuals and organizations can make informed decisions about true application security risks.” The organization believes that by promoting the importance of application security, it can help individuals and organizations to better protect their data and systems from cyber attacks.
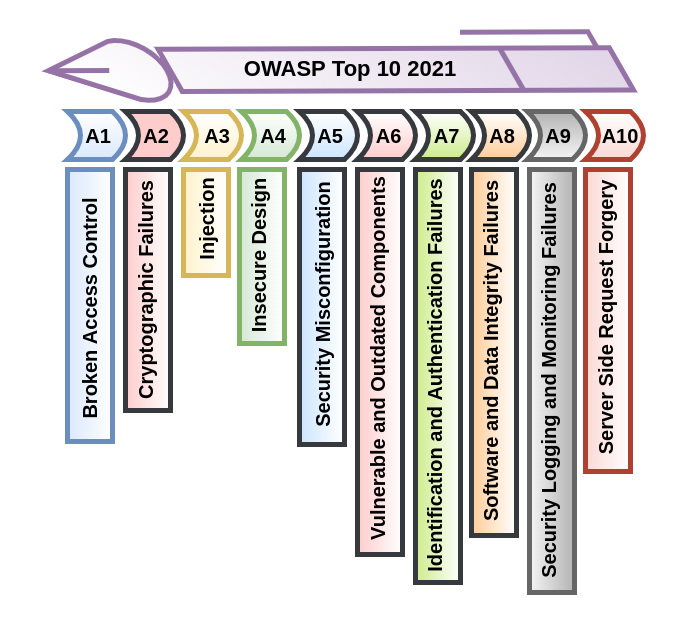
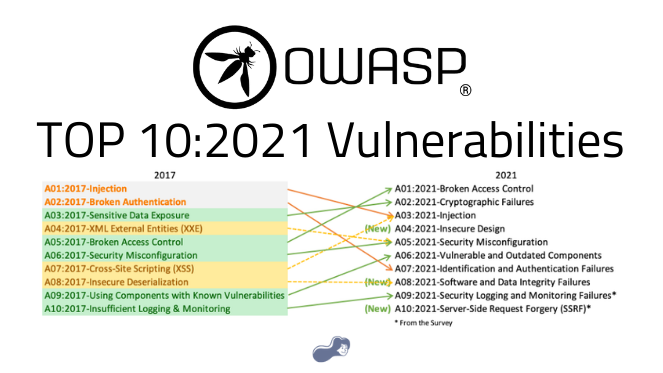
OWASP Top 10 2021: The Risks Associated With Each Vulnerability
A01-2021: Broken Access Control
Broken access controls are a type of security vulnerability that occurs when an application fails to properly enforce access controls, allowing unauthorized users to access sensitive data or perform unauthorized actions within the application. This vulnerability can be exploited by attackers to steal sensitive information, modify data, or perform other malicious actions within the application.
Common examples of broken access control include insecure direct object references, where an attacker is able to directly access and modify sensitive data without proper authorization, and insufficient authorization checks, where an attacker is able to access sensitive data or perform unauthorized actions by bypassing access control mechanisms.
To prevent broken access control vulnerabilities, developers should implement proper access control mechanisms, such as role-based access control (RBAC) or attribute-based access control (ABAC), to ensure that users are only able to access the data and perform the actions that they are authorized to do so.
In addition, developers should use secure coding practices, such as input validation and output encoding, to prevent attackers from bypassing access control mechanisms through input manipulation or other methods.
Regular testing and monitoring of access controls can also help to identify and prevent broken access control vulnerabilities. This includes conducting vulnerability assessments and penetration testing to identify potential vulnerabilities and taking steps to address any identified issues.
Broken access control vulnerabilities pose a significant risk to the security of web applications, and developers and security professionals must take proactive steps to prevent these types of attacks by implementing proper security controls and best practices.
A02-2021: Cryptographic Failures
Cryptographic failures are security vulnerabilities that arise from weaknesses or flaws in cryptographic algorithms or implementations. Cryptography is the practice of using mathematical algorithms to protect the confidentiality, integrity, and authenticity of information transmitted over a network or stored on a computer system. Cryptographic failures can occur when encryption keys are compromised, when algorithms are weak, or when cryptographic protocols are implemented incorrectly.
Examples of cryptographic failures include:
Weak encryption algorithms: Weak encryption algorithms such as DES or WEP are susceptible to brute-force attacks, which can allow an attacker to decrypt encrypted data.
Key management failures: Cryptographic keys used for encryption and decryption are sensitive pieces of information that must be kept secure. Key management failures can occur when keys are not properly generated, stored, or destroyed.
Protocol weaknesses: Cryptographic protocols such as SSL or TLS are designed to provide secure communication over a network. However, weaknesses in these protocols can lead to man-in-the-middle attacks, which can allow an attacker to intercept and modify data in transit.
Side-channel attacks: Cryptographic algorithms can sometimes leak information about the encrypted data through side-channels such as power consumption, electromagnetic radiation, or timing information. This can allow an attacker to recover the plaintext message from the ciphertext.
Developers and security professionals must implement strong encryption algorithms and protocols that are resistant to attacks. They must also implement proper key management practices to ensure that cryptographic keys are generated, stored, and destroyed securely. Additionally, regular testing and monitoring of cryptographic implementations can help to identify and prevent potential vulnerabilities.
Cryptographic failures can have severe consequences for the security of web applications and other computer systems. By implementing strong encryption algorithms and protocols, properly managing cryptographic keys, and regularly testing and monitoring cryptographic implementations, organizations can reduce the risk of cryptographic failures and other security threats.
OWASP - Cryptographic Failures
A03-2021: Injection Attacks
Injection attacks are a type of security vulnerability that can have severe consequences if not properly addressed. Injection attacks occur when an attacker is able to inject malicious code or input into an application, with the intention of manipulating the behavior of the application.
The most common type of injection attack is a SQL injection, where an attacker injects SQL code into an input field of an application, such as a search bar or login field. The goal of an SQL injection attack is usually to gain unauthorized access to sensitive data or to modify or delete data within the application’s database.
Other types of injection attacks include LDAP injection, XPath injection, and OS command injection, where an attacker is able to manipulate the behavior of an application by injecting malicious input into fields that are used to execute LDAP, XPath or OS commands respectively.
The consequences of an injection attack can be significant, including data theft, data loss or corruption, unauthorized access, and system compromise. The impact of these attacks can be especially severe for applications that process sensitive data, such as financial or healthcare applications.
To prevent injection attacks, developers should use secure coding practices, such as input validation and parameterized queries, to ensure that user input is properly sanitized and validated. In addition, applications should be regularly tested for vulnerabilities, and any identified vulnerabilities should be promptly addressed.
Injection attacks are a significant threat to the security of software applications, and developers and security professionals should take steps to mitigate the risk of these attacks by implementing proper security measures.
A04-2021: Insecure Design
Insecure design vulnerabilities refer to security weaknesses that arise from poor design decisions or flawed architecture in software systems. These vulnerabilities can allow an attacker to exploit flaws in the design of the system to gain unauthorized access to data or carry out other malicious activities.
Insecure design vulnerabilities include:
Lack of input validation: Applications that do not properly validate user input can be vulnerable to injection attacks such as SQL injection or cross-site scripting (XSS).
Weak authentication and authorization mechanisms: Applications that rely on weak authentication and authorization mechanisms can be vulnerable to attacks such as brute-force attacks or session hijacking.
Inadequate error handling: Applications that do not properly handle errors can provide valuable information to attackers that can be used to carry out further attacks.
Insufficient separation of privileges: Applications that do not separate privileges between different roles or users can allow attackers to gain access to sensitive data or carry out unauthorized actions.
To prevent this vulnerability, developers and security professionals must follow secure design principles and best practices when designing software systems. This includes properly validating all user input, implementing strong authentication and authorization mechanisms, and properly handling errors.
Developers should conduct regular threat modeling exercises to identify potential vulnerabilities and implement appropriate security controls to mitigate them. This includes designing software systems with the principle of least privilege in mind, ensuring that privileges are separated between different roles and users.
Insecure design vulnerabilities can have severe consequences for the security of web applications and other software systems. By following secure design principles and best practices, regularly conducting threat modeling exercises, and implementing appropriate security controls, developers and security professionals can reduce the risk of insecure design vulnerabilities and other security threats.
A05-2021: Security Misconfiguration
Security misconfigurations are a type of security vulnerability that occurs when an application or system is not configured properly, leaving it open to attacks or other security risks. This vulnerability can occur due to a variety of reasons, such as default configurations, outdated software, or improper settings.
Common examples of security misconfiguration include leaving default passwords or credentials in place, failing to apply security patches or updates to software, and leaving unnecessary services or ports open.
To prevent security misconfiguration vulnerabilities, developers and system administrators should follow secure configuration practices, such as applying security updates and patches in a timely manner, using strong passwords and multi-factor authentication, and disabling unnecessary services or ports.
In addition, regular security audits and vulnerability assessments can help to identify potential security misconfigurations and other vulnerabilities, allowing developers and administrators to take steps to address these issues before they can be exploited by attackers.
Security misconfiguration vulnerabilities pose a significant risk to the security of web applications and systems, and developers and security professionals must take proactive steps to prevent these types of attacks by implementing proper security controls and best practices. By following secure configuration practices and regularly testing and monitoring systems for vulnerabilities, organizations can reduce the risk of security misconfiguration and other security threats.
OWASP - Security Misconfigurations
A06-2021: Vulnerable and Outdated Components
Vulnerable and outdated components are security weaknesses that arise from the use of third-party software components with known security vulnerabilities or outdated versions of software components that are no longer supported by the vendor. These vulnerabilities can allow an attacker to exploit flaws in the components to gain unauthorized access to data or carry out other malicious activities.
Vulnerable and outdated components include:
Unpatched software vulnerabilities: Applications that use outdated versions of software components with known security vulnerabilities are vulnerable to attacks that exploit these vulnerabilities.
Insecure libraries: Applications that use insecure libraries, such as OpenSSL, that have known security vulnerabilities can be exploited by attackers to gain unauthorized access to data.
Deprecated software: Applications that use software that is no longer supported by the vendor, such as Windows XP, are vulnerable to attacks that exploit known vulnerabilities in the software.
To prevent this, developers and security professionals must monitor and maintain the software components used in their applications. This includes regularly updating and patching software components to address known vulnerabilities and ensuring that all components are still supported by the vendor.
Additionally, developers and/or development teams should conduct regular vulnerability scans and penetration tests to identify potential vulnerabilities in their applications and take appropriate steps to mitigate them. This may include removing insecure or unnecessary components, upgrading to newer versions of components, or implementing additional security controls to mitigate potential vulnerabilities.
This type of vulnerability can have severe consequences for the security of web applications and other software systems. By monitoring and maintaining the software components used in their applications, regularly updating and patching components, and conducting regular vulnerability scans and penetration tests, developers and security professionals can reduce the risk of vulnerable and outdated components and other security threats.
OWASP - Vulnerable and Outdated Components
A07-2021: Identification and Authentication Failures
Identification and authentication failures refer to security weaknesses that arise from flaws in the way that users are identified and authenticated in web applications and other software systems. These vulnerabilities can allow an attacker to gain unauthorized access to data or carry out other malicious activities by bypassing the authentication mechanism.
Identification and authentication failures include:
Weak password policies: Applications that do not enforce strong password policies are vulnerable to brute-force attacks and password guessing.
Insufficient account lockout policies: Applications that do not lock user accounts after a certain number of failed login attempts are vulnerable to brute-force attacks.
Insecure password storage: Applications that store passwords in plaintext or use weak encryption algorithms are vulnerable to password theft.
Lack of multi-factor authentication: Applications that rely on single-factor authentication, such as username and password, are vulnerable to attacks that bypass the authentication mechanism.
To prevent identification and authentication failures, developers and security professionals must implement strong identification and authentication mechanisms that adhere to industry best practices. This includes enforcing strong password policies, implementing multi-factor authentication, and using secure password storage mechanisms such as hash functions with salt.
Also, developers should conduct regular vulnerability scans and penetration tests to identify potential vulnerabilities in their authentication mechanisms and take appropriate steps to mitigate them. This may include implementing additional security controls, such as rate limiting and account lockout policies, to prevent brute-force attacks.
Identification and authentication failures can have severe consequences for the security of web applications and other software systems. By implementing strong identification and authentication mechanisms, adhering to industry best practices, and conducting regular vulnerability scans and penetration tests, developers and security professionals can reduce the risk of identification and authentication failures and other security threats.
OWASP - Identification and Authentication Failures
A08-2021: Software and Data Integrity Failures
Software and data integrity failures refer to security weaknesses that arise from flaws in the way that software and data are stored, processed, and transmitted. These vulnerabilities can allow an attacker to manipulate or destroy data, compromise the integrity of software, or carry out other malicious activities.
Some examples of software and data integrity failures include:
Code injection attacks: Applications that lack properly sanitize user input are vulnerable to code injection attacks, where an attacker can inject malicious code into the application to carry out unauthorized activities.
Man-in-the-middle attacks: Applications that aren’t using secure communication protocols, such as SSL or TLS, are vulnerable to man-in-the-middle attacks, where an attacker can intercept and modify data transmitted between the client and server.
File inclusion vulnerabilities: Applications that don’t properly validate user input in file inclusion mechanisms, such as include or require statements, are vulnerable to file inclusion attacks, where an attacker can include malicious code into the application.
Data tampering: Applications that do not properly validate user input or protect against unauthorized modifications are vulnerable to data tampering attacks, where an attacker can modify or delete data stored in the application.
To prevent these failures, developers and security professionals must implement strong security controls that ensure the integrity of software and data. This includes implementing input validation and output encoding mechanisms to prevent code injection attacks, using secure communication protocols to prevent man-in-the-middle attacks, and implementing access controls and data encryption to protect against data tampering and unauthorized modifications.
Also, developers should conduct regular vulnerability scans and penetration tests to identify potential vulnerabilities in their software and data storage mechanisms and take appropriate steps to mitigate them. This may include implementing additional security controls, such as intrusion detection systems and integrity monitoring tools, to detect and prevent unauthorized modifications to software and data.
Software and data integrity failures can have severe consequences for the security of web applications and other software systems. By implementing strong security controls, adhering to industry best practices, and conducting regular vulnerability scans and penetration tests, developers and security professionals can reduce the risk of software and data integrity failures and other security threats.
OWASP - Software and Data Integrity Failures
A09-2021: Security Logging and Monitoring Failures
Security logging and monitoring failures refer to security weaknesses that arise from flaws in the way that security logs are generated, stored, and monitored. These vulnerabilities can allow an attacker to carry out malicious activities without being detected, or can prevent security teams from identifying and responding to security incidents in a timely manner.
Security logging and monitoring failures include:
Insufficient logging: Applications that do not generate sufficient security logs are vulnerable to attacks that cannot be detected or traced back to the attacker.
Lack of real-time monitoring: Applications that do not implement real-time monitoring mechanisms are vulnerable to attacks that can go undetected for long periods of time, allowing attackers to carry out further malicious activities.
Incomplete log analysis: Applications that do not properly analyze and correlate security logs are vulnerable to attacks that can be disguised or split across multiple logs, making them difficult to identify.
Limited incident response capabilities: Applications that do not have a defined incident response process or lack the necessary tools and expertise to respond to security incidents are vulnerable to prolonged and more severe attacks.
To prevent these failures, developers and security professionals must implement strong security logging and monitoring mechanisms that adhere to industry best practices. This includes generating sufficient security logs that capture all relevant events, implementing real-time monitoring mechanisms that detect security incidents as they occur, and conducting comprehensive log analysis to identify potential security threats.
Also, developers should conduct regular vulnerability scans and penetration tests to identify potential vulnerabilities in their security logging and monitoring mechanisms and take appropriate steps to mitigate them. This may include implementing additional security controls, such as intrusion detection systems and security information and event management (SIEM) tools, to improve their incident response capabilities.
Security logging and monitoring failures can have severe consequences for the security of web applications and other software systems. By implementing strong security logging and monitoring mechanisms, adhering to industry best practices, and conducting regular vulnerability scans and penetration tests, developers and security professionals can reduce the risk of security logging and monitoring failures and other security threats.
OWASP - Security Logging and Monitoring Failures
A10-2021: Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) is a type of web application vulnerability that allows an attacker to send unauthorized requests from a vulnerable server to other internal or external systems. SSRF attacks can be used to bypass security controls, access sensitive information, or carry out further attacks on other systems.
SSRF attacks typically involve exploiting web application functionality that allows the application to send requests to other systems. This functionality can be used by an attacker to send requests to internal systems, such as databases or other backend servers, or to external systems, such as cloud services or other web applications.
Examples of SSRF vulnerabilities include:
Malicious URL redirection: An attacker can craft a malicious URL that redirects the vulnerable server to a target system, allowing the attacker to access sensitive information or carry out further attacks.
Request smuggling: An attacker can manipulate the HTTP request headers to trick the vulnerable server into sending requests to other systems.
Proxy abuse: An attacker can use the vulnerable server as a proxy to access other systems, bypassing any security controls in place.
To prevent these attacks, developers should implement strong input validation and output encoding mechanisms to prevent attackers from injecting malicious requests into the web application. This may include implementing a whitelist of allowed URLs or IP addresses, using DNS resolution to validate external URLs, and restricting access to internal systems.
Also, developers should conduct regular vulnerability scans and penetration tests to identify potential SSRF vulnerabilities and take appropriate steps to mitigate them. This may include implementing additional security controls, such as web application firewalls or network segmentation, to prevent attackers from accessing sensitive systems.
SSRF attacks can have severe consequences for the security of web applications and other software systems. By implementing strong security controls, adhering to industry best practices, and conducting regular vulnerability scans and penetration tests, developers and security professionals can reduce the risk of SSRF attacks and other security threats.
OWASP - Server Side Request Forgery SSRF
Conclusion
Developers should conduct regular vulnerability scans and penetration tests to identify potential vulnerabilities and take appropriate steps to mitigate them.
The OWASP Top 10 is an important tool for software developers and security professionals. By understanding the vulnerabilities outlined in the OWASP Top 10, developers can take steps to improve the security of their applications and protect against common attack vectors. It is important to keep in mind that the OWASP Top 10 is not a comprehensive list of all possible vulnerabilities, and developers should take a holistic approach to application security.
1
2
3
┌──(robert㉿kali)-[~]
└─$ docker run -t owasp/zap2docker-stable zap-full-scan.py -t http://yourwebsite.com
...