In 2010, a computer worm known as Stuxnet made headlines around the world. Its target was an Iranian nuclear facility, and it was designed to disrupt and damage the centrifuges used in the facility’s uranium enrichment program. Stuxnet was unlike any other malware that had been seen before, and it raised important questions about the growing threat of cyber attacks on critical infrastructure.
Computer Worms
To understand Stuxnet, we need to understand what a computer worm is. A computer worm is a type of malware that is designed to spread from computer to computer. Unlike viruses, which need a host program to replicate, worms are self-replicating and can spread without any human intervention.
Forbes - The Story Behind The Stuxnet Virus
Computer worms can be used for a variety of reasons, from stealing sensitive data to launching denial-of-service attacks. Some worms are designed to create backdoors into computer systems, which can then be exploited by attackers to gain access to sensitive data or to launch further attacks.
Stuxnet: A Sophisticated Worm
Stuxnet wasn’t the first computer worm to make headlines, but it was arguably the most sophisticated. It was designed to target a specific type of industrial control system called a programmable logic controller (PLC). PLCs are used to control machinery in factories, power plants, and other critical infrastructure.
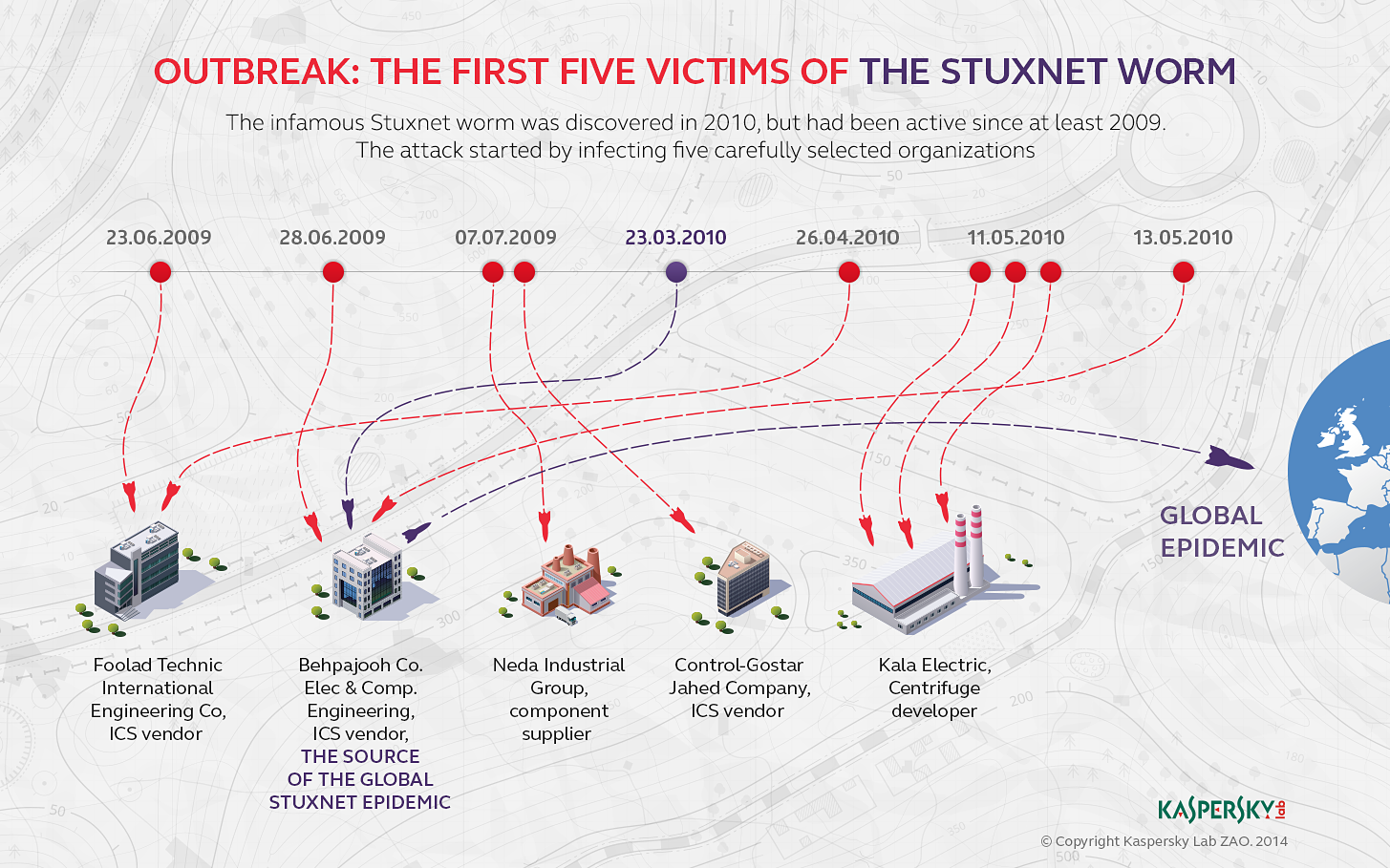
Stuxnet was designed to be delivered through USB drives, and it was programmed to search for specific PLCs that were used in the Iranian nuclear facility. Once it infected a PLC, it would lie dormant for a period of time before activating and causing the centrifuges to spin out of control. This caused significant damage to the facility’s infrastructure, and it set back Iran’s nuclear program by several years.
Time of Israel - ‘Dutch mole’ planted Stuxnet virus in Iran nuclear site on behalf of CIA, Mossad
The Rootkit
As a rootkit, Stuxnet, was able to conceal its presence in multiple ways. It used a combination of kernel-mode drivers, file-system filters, and other techniques to hide files and processes from both the operating system and the user. It also employed a number of anti-debugging and anti-analysis techniques to make it difficult for security researchers to study its behavior.
The rootkit component of Stuxnet was critical to its success, as it allowed the malware to remain undetected on infected systems for an extended period of time. This gave it ample opportunity to spread through Iran’s nuclear program and carry out its mission of disrupting the centrifuges used to enrich uranium.
Stuxnet is the most famous rootkit as of this writing.
Origins of Stuxnet
The origins of Stuxnet are still shrouded in mystery, but it is widely believed to have been a joint operation between the United States and Israel. The worm was first discovered by a Belarusian security company, and it quickly became clear that it was unlike any other malware that had been seen before.
Smithsonian Magazine - Richard Clarke on Who Was Behind the Stuxnet Attack
The fact that Stuxnet was designed to target a specific type of industrial control system raised important questions about the use of cyber attacks in warfare. Some experts argue that Stuxnet was a game-changer, and that it opened the door to a new era of cyber warfare.
Protecting Against Worms
Computer worms are a serious threat to cybersecurity, and they can cause significant damage if they are not detected and stopped. There are several steps that individuals and organizations can take to protect themselves against worms and other types of malware.
First and foremost, it is important to keep software up-to-date with the latest security patches. Many worms and other types of malware exploit known vulnerabilities in software, and keeping software updated can help prevent these attacks.
It is also important to use antivirus software and to scan all files before opening them. Many worms are spread through email attachments or malicious websites, and scanning files before opening them can help prevent infection.
Finally, it is important to be cautious when plugging any input output peripheral into computer systems. Stuxnet was able to spread through USB drives, and many other worms use similar methods. Avoid using USB drives from unknown sources, and scan all external devices before using them.
Security.org - What Is a Computer Worm & How Do You Prevent Them?

1
2
3
4
┌──(robert㉿kali)-[~]
└─$ shutdown -h now
SHUTDOWN DENIED
You are here -{FOREVER!}