In May 2017, the WannaCry ransomware attack had a significant impact on organizations globally. The attack spread rapidly across different countries, infecting over 200,000 computers and causing significant disruptions to various industries. WannaCry is an example of the destructive and costly nature of cyber threats, making it essential to understand how it occurred, and how it could have been prevented. We will delve into the details of the WannaCry ransomware attack, its impact, response, and lessons learned. Examining this case study, we can gain insights into the importance of cyber-security and the need for organizations to take proactive measures to protect themselves from such threats.
Impact of the Attack
The impact of the WannaCry was widespread, affecting both individuals and organizations globally. The attack caused disruptions in several industries, resulting in the shutdown of hospitals, transportation systems, and manufacturing plants, among others. The financial impact was estimated to be in the billions of dollars, with companies facing losses due to halted operations and lost data. The attack also highlighted the vulnerability of critical infrastructure, raising concerns about the potential for future attacks on essential services such as healthcare and transportation. Additionally, the attack eroded trust in the affected organizations, and many individuals were left feeling vulnerable and exposed. The WannaCry ransomware attack demonstrated the catastrophic consequences that cyber threats can have on organizations and the wider society.
Why WannaCry Was so Effective
This ransomware attack was particularly effective for several reasons:
Firstly, the attack targeted a vulnerability in the SMB protocol that was widely used and affected older versions of Microsoft Windows that had not been updated with the latest security patches. This made it easy for the attackers to infect machines that had not taken necessary security measures.
Secondly, the ransomware used a worm-like functionality that allowed it to spread rapidly across networks and infect other machines connected to the infected computer. This feature made it easier for the attackers to propagate the ransomware and infect a large number of systems quickly.
Thirdly, the attackers demanded payment in Bitcoin, a cryptocurrency that is difficult to trace and has a high level of anonymity, making it easier for the attackers to collect the ransom and evade law enforcement.
Finally, the attackers used social engineering tactics to lure victims into opening infected attachments or clicking on malicious links, exploiting the human element in cybersecurity.
This attack combined technical vulnerabilities with social engineering tactics, allowing the attackers to propagate the ransomware quickly and widely and demand payment in a difficult-to-trace cryptocurrency.
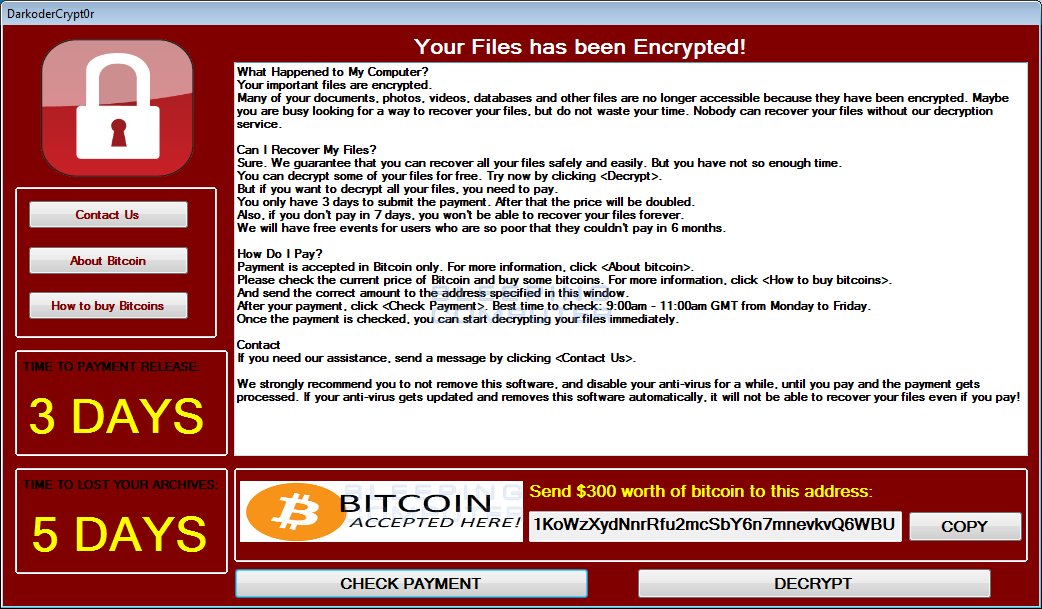
WannaCry Origins
WannaCry itself was developed using a tool called EternalBlue, which was leaked from the US National Security Agency (NSA). The attackers also used other tools and techniques, including the DoublePulsar backdoor, to exploit and gain access to vulnerable systems.
Wired - The Leaked NSA Spy Tool That Hacked the World
The creators of WannaCry are not known for certain, but the attack was attributed to a group called Lazarus, which is believed to be based in North Korea. Lazarus has been linked to several high-profile attacks, including the 2014 Sony Pictures hack and the theft of $81 million from the Bangladesh Bank in 2016.
Trend Micro -A Look into the Lazarus Group’s Operations
The Killswitch and Marcus Hutchins
This attack could have been much worse if not for the discovery of a hidden feature within the ransomware known as the “killswitch.” The killswitch was essentially a safety mechanism built into the ransomware, which allowed the attackers to stop the spread of the malware if they chose to do so.
The killswitch was discovered by a young cybersecurity researcher named Marcus Hutchins, who was only 22 years old at the time. Hutchins was working from his bedroom in the UK when he noticed that the ransomware was attempting to connect to a specific domain name. He decided to register the domain name himself, which effectively acted as a killswitch and prevented the ransomware from spreading further.
Hutchins’ discovery was a significant breakthrough in the fight against the WannaCry attack. Cybersecurity experts were able to use the killswitch to contain the spread of the ransomware and prevent further damage. Hutchins became an overnight hero in the cybersecurity community, with many praising him for his quick thinking and ingenuity.
Wired - How an Accidental ‘Kill Switch’ Slowed Friday’s Massive Ransomware Attack

Lessons Learned from WannaCry
The WannaCry attack was one of the most widespread cyber attacks in history. The attack affected over 200,000 computers in more than 150 countries, causing significant disruption to businesses, hospitals, and government agencies. The attack was a wake-up call for many organizations and individuals, highlighting the need for improved cybersecurity practices and awareness. In this article, we will discuss the key lessons learned from the WannaCry ransomware attack.
Keeping software up to date
- One of the primary reasons why the WannaCry ransomware attack was so effective was that it exploited a vulnerability in the SMB protocol that had been patched by Microsoft several months before the attack. Organizations and individuals must ensure that their software is up to date and that they have applied the latest security patches to prevent vulnerabilities from being exploited.
Importance of backups
- Files on infected machines were encrypted, making it impossible to access them without the decryption key. Organizations and individuals should regularly back up their data to ensure that they can recover their data in the event of a ransomware attack.
A need for a comprehensive cybersecurity strategy
- WannaCry demonstrated the need for a comprehensive cybersecurity strategy that includes a combination of technical measures, such as firewalls and antivirus software, and non-technical measures, such as security awareness training for employees. It is essential to have a plan in place to prevent, detect, and respond to cyber attacks.
Dangers of relying on legacy systems
- WannaCry ransomware primarily affected older versions of the Microsoft Windows operating system that had not been updated with the latest security patches. Organizations should consider upgrading to newer systems that are less vulnerable to attacks. Relying on legacy systems can increase the risk of cyber attacks.
Importance of collaboration
- This attack highlighted the need for collaboration between organizations, law enforcement agencies, and cybersecurity experts to prevent and respond to cyber threats. Collaboration can help organizations and individuals stay ahead of attackers and mitigate the impact of attacks when they occur.
Conclusion
WannaCry was a stark reminder of the importance of cybersecurity. Organizations and individuals must take steps to protect their systems and data from cyber attacks. By keeping software up to date, regularly backing up data, implementing a comprehensive cybersecurity strategy, upgrading legacy systems, and collaborating with others, we can reduce the risk of cyber attacks and mitigate their impact.
1
2
3
4
┌──(robert㉿kali)-[~]
└─$ cat wannacry.txt
When infected you just wanna cry...

