Some cyber attacks are more impressive than others while causing significant damage to systems, networks, and organizations.
The Zero-Day Exploit
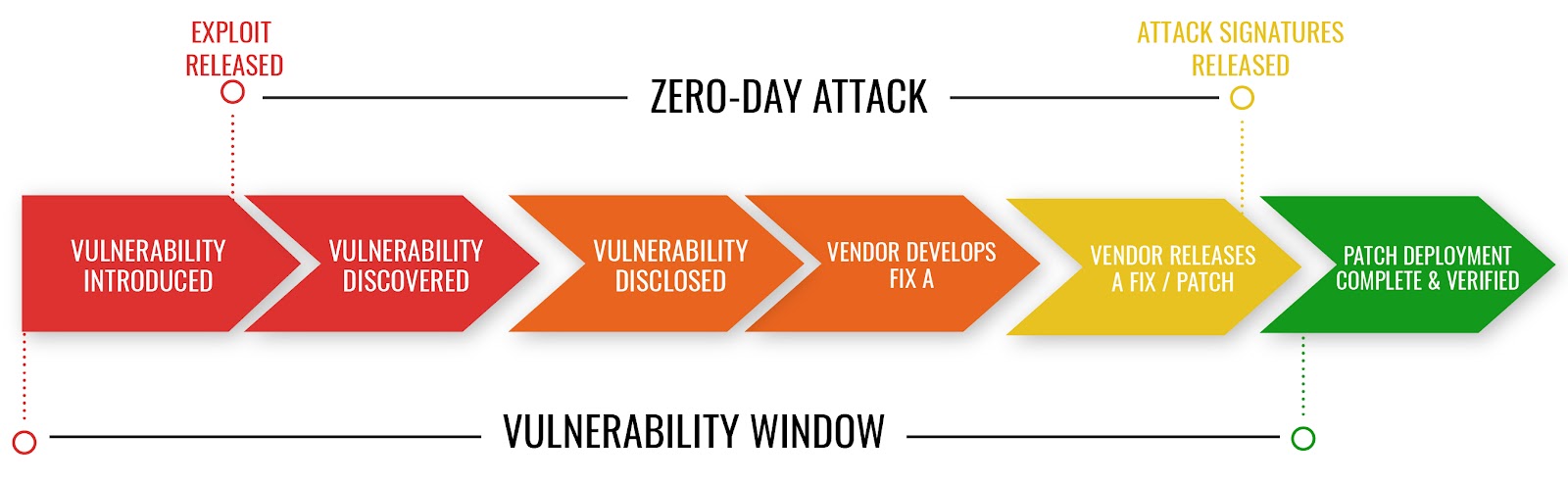
A Zero-Day exploit is a type of attack that targets vulnerabilities in software that haven’t been discovered or patched by the software developers. Because these vulnerabilities are unknown to the software developers, there are no patches or updates available to fix them. As a result, attackers can use these vulnerabilities to gain access to systems, steal sensitive information, or carry out other malicious activities.
This type of attack will often be performed by advanced persistent threat (APT) groups, who are highly skilled and motivated attackers that typically target government agencies, defense contractors, and other high-value targets. APT groups are known for using sophisticated techniques and tactics to infiltrate systems, such as spear-phishing campaigns and social engineering tactics.
Zero-Day attacks can be particularly disruptive because they can go undetected for long periods of time, allowing attackers to carry out their activities undetected. Once the vulnerability is discovered and exploited, it can be difficult to remediate, and the impact of the attack can be significant.
Stuxnet Worm
One example of a Zero-Day is the Stuxnet worm, which was discovered in 2010. Stuxnet was a highly sophisticated malware attack that targeted industrial control systems (ICS) used in nuclear power plants and other critical infrastructure. The attack was believed to have been carried out by the US and Israel, and it caused significant damage to Iran’s nuclear program.
Prevention
Preventing Zero-Day attacks can be challenging, but there are steps that organizations can take to reduce their risk. Regularly updating software and systems with the latest patches and updates is one of the most effective ways to prevent Zero-Day exploits. Organizations can also implement intrusion detection systems and other security tools to detect and respond to suspicious activities.
Conclusion
Zero-Day attacks are very disruptive cyber attacks, and they can cause significant damage to systems, networks, and organizations. By understanding the nature of these attacks and taking proactive steps to prevent them, businesses and individuals can protect themselves from these threats and reduce their risk of falling victim to cyber attacks.
1
2
3
4
5
6
7
┌──(robert㉿kali)-[~]
└─$ python3 zero-day.py 172.168.100.17
[!] Exploited
[+] Session 1 Connected 172.168.100.17
$ pwd
/