STIG Solutions [NG]
Author: Alexander Hillock
Framework Category: Operate and Maintain
Specialty Area: Systems Analysis
Work Role: Systems Security Analyst
Task Description: Implement security measures to resolve vulnerabilities, mitigate risks, and recommend security changes to system or system components as needed. (T0485)
Scenario
After a review, I was made aware that some of our computers are not up to security configuration standards, leaving the machines open to multiple vulnerabilities that could be catastrophic if exploited. I need you to configure specific machines to comply with specific configurations found in DISA’s (Defense Information Systems Agency) Security Technical Implementation Guide.
Additional Information
More details and objectives about this challenge will be introduced during the challenge meeting, which will start once you begin deploying the challenge.
You will be able to check your progress during this challenge using the check panel within the workspace once the challenge is deployed. The checks within the check panel report on the state of some or all of the required tasks within the challenge.
Once you have completed the requested tasks, you will need to document the methodology you used with as much detail and professionalism as necessary. This should be done on the documentation tab within the workspace once the challenge is deployed. Below the main documentation section be sure to include a tagged list of applications you used to complete the challenge.
Your username/password to access all virtual machines and services within the workspace will be the following… Username: playerone Password: password123
The username/password used to access the Firewall’s web interface within the workspace will be the following… Username: admin Password: password123
Mission Start
I began work on this challenge on 5 MAR 2022, at at 15:45 hours, with the following meeting:
Gary Thatcher:
@playerone, It looks like some of our machines aren’t as secure as we might have thought, there is some configuration I’d like you to perform on the Prod-Web machine to close up some of the holes that are there.
Ione Leventis:
I’ve done some research for a good configuration guide and I’ve found something called a Security Technical Implementation Guide. I’ve gone ahead and dropped both the guide and the viewing tool on the Security-Desk. You should make sure the machine is configured with some of the CAT II specifications. Specifically, I have a range of the CAT II configs I’ll want you to implement.
Richard LeGrand:
WE HAVE VULNERABILITIES??!!! WHAT IS GOING ON??? GET THIS FIXED….YESTERDAY!!!!!!
Ione Leventis:
For now, I want you fix any findings you come accross within the range of rule 13 (V-204406) through rule 31 (V-204426). Just make sure you’re filtering via only CAT II rules. However, if you come accross any user specific fixes, please leave the nagios account alone, otherwise our MSP wont be able to monitor our environment anymore and that will cause a lot headaches for everyone.
Ione Leventis:
Oh, and make sure you don’t unzip the Red Hat Enterprise Linux STIG, just import it straight into the viewer itself. I know our Prod-Web is CentOS 7 but the rules I need you to cover will still apply. Keep in mind the STIG and STIG Viewer are both located on the Security-Desk, however the issues you will be solving are on Prod-Web.


I logged into the Security-Desk, after the meeting, and used an ssh connection into Prod-Web.

I used the STIG viewer on the Security-Desk to filter and view the STIG rules that needed to be applied beginning with:

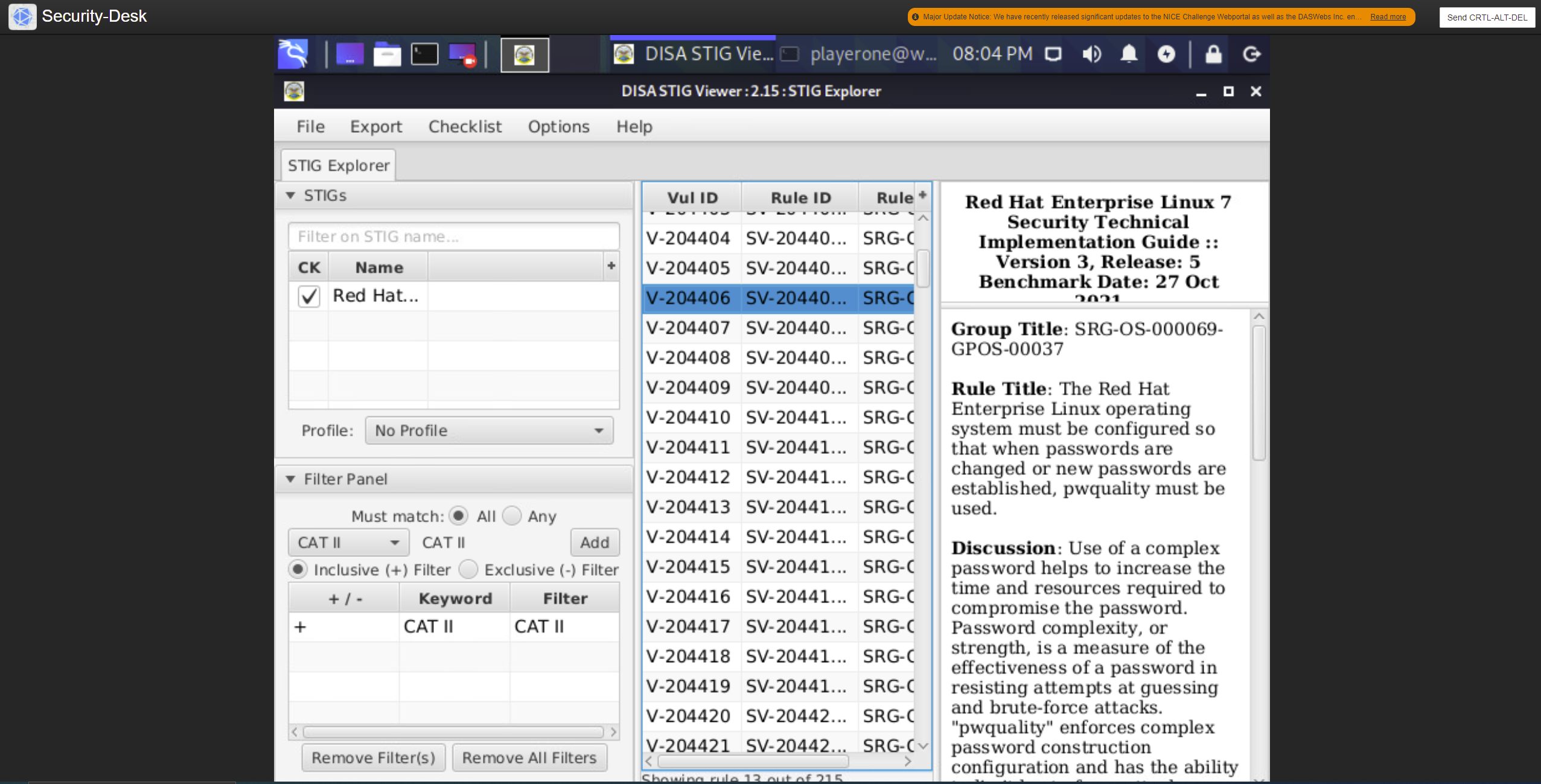
Vul ID V-204406
Check Text: Verify the operating system uses “pwquality” to enforce the password complexity rules.
Check for the use of “pwquality” with the following command:
1
$ cat /etc/pam.d/system-auth | grep pam_pwquality
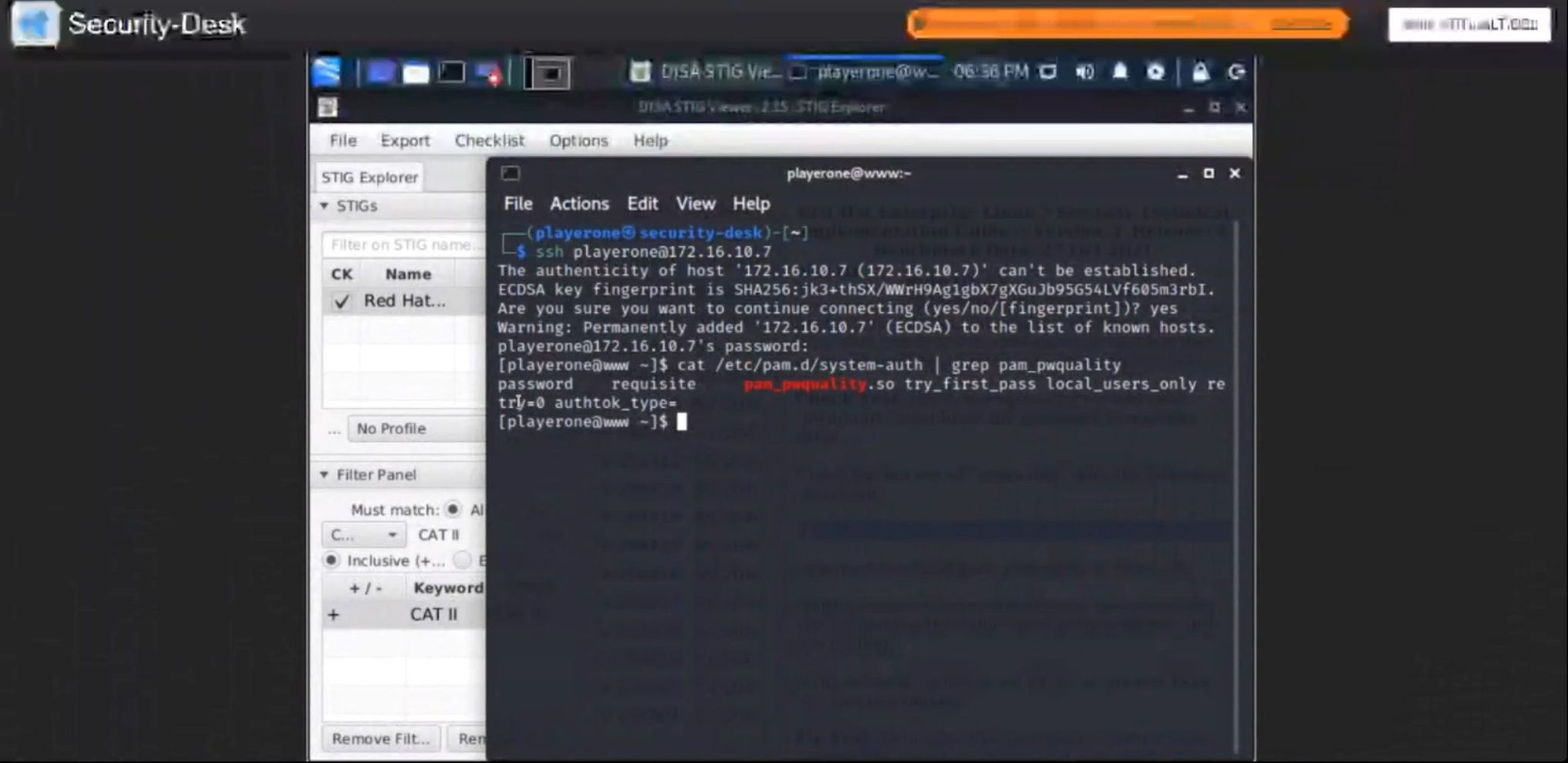
password required pam_pwquality.so retry=3
If the command does not return an uncommented line containing the value “pam_pwquality.so”, this is a finding.
If the value of “retry” is set to “0” or greater than “3”, this is a finding.
Fix Text: Configure the operating system to use “pwquality” to enforce password complexity rules.
Add the following line to “/etc/pam.d/system-auth” (or modify the line to have the required value):
1
$ sudo vim /etc/pam.d/system-auth

password required pam_pwquality.so retry=3
Note: The value of “retry” should be between “1” and “3”.

Vul ID V-204407
Check Text: Note: The value to require a number of upper-case characters to be set is expressed as a negative number in “/etc/security/pwquality.conf”.
Check the value for “ucredit” in “/etc/security/pwquality.conf” with the following command:
1
$ grep ucredit /etc/security/pwquality.conf
ucredit = -1
If the value of “ucredit” is not set to a negative value, this is a finding.
Fix Text: Configure the operating system to enforce password complexity by requiring that at least one upper-case character be used by setting the “ucredit” option.
Add the following line to “/etc/security/pwquality.conf” (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
ucredit = -1
Vul ID V-204408
Check Text: Note: The value to require a number of lower-case characters to be set is expressed as a negative number in “/etc/security/pwquality.conf”.
Check the value for “lcredit” in “/etc/security/pwquality.conf” with the following command:
1
$ grep lcredit /etc/security/pwquality.conf
lcredit = -1
If the value of “lcredit” is not set to a negative value, this is a finding.
Fix Text: Configure the system to require at least one lower-case character when creating or changing a password.
Add or modify the following line in “/etc/security/pwquality.conf”:
1
$ sudo vim /etc/security/pwquality.conf
lcredit = -1
Vul ID V-204409
Check Text: Note: The value to require a number of numeric characters to be set is expressed as a negative number in “/etc/security/pwquality.conf”.
Check the value for “dcredit” in “/etc/security/pwquality.conf” with the following command:
1
$ grep dcredit /etc/security/pwquality.conf
dcredit = -1
If the value of “dcredit” is not set to a negative value, this is a finding.
Fix Text: Configure the operating system to enforce password complexity by requiring that at least one numeric character be used by setting the “dcredit” option.
Add the following line to /etc/security/pwquality.conf (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
dcredit = -1
Vul ID V-204410
Check Text: Verify the operating system enforces password complexity by requiring that at least one special character be used.
Note: The value to require a number of special characters to be set is expressed as a negative number in “/etc/security/pwquality.conf”.
Check the value for “ocredit” in “/etc/security/pwquality.conf” with the following command:
1
$ grep ocredit /etc/security/pwquality.conf
ocredit=-1
If the value of “ocredit” is not set to a negative value, this is a finding.
Fix Text: Configure the operating system to enforce password complexity by requiring that at least one special character be used by setting the “ocredit” option.
Add the following line to “/etc/security/pwquality.conf” (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
ocredit = -1
Vul ID V-204411
Check Text: The “difok” option sets the number of characters in a password that must not be present in the old password.
Check for the value of the “difok” option in “/etc/security/pwquality.conf” with the following command:
1
$ grep difok /etc/security/pwquality.conf
difok = 8
If the value of “difok” is set to less than “8”, this is a finding.
Fix Text: Configure the operating system to require the change of at least eight of the total number of characters when passwords are changed by setting the “difok” option.
Add the following line to “/etc/security/pwquality.conf” (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
difok = 8
Vul ID V-204412
Check Text: The “minclass” option sets the minimum number of required classes of characters for the new password (digits, upper-case, lower-case, others).
Check for the value of the “minclass” option in “/etc/security/pwquality.conf” with the following command:
1
$ grep minclass /etc/security/pwquality.conf'
minclass = 4
If the value of “minclass” is set to less than “4”, this is a finding.
Fix Text: Configure the operating system to require the change of at least four character classes when passwords are changed by setting the “minclass” option.
Add the following line to “/etc/security/pwquality.conf conf” (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
minclass = 4
Vul ID V-204413
Check Text: The “maxrepeat” option sets the maximum number of allowed same consecutive characters in a new password.
Check for the value of the “maxrepeat” option in “/etc/security/pwquality.conf” with the following command:
1
$ grep maxrepeat /etc/security/pwquality.conf'
maxrepeat = 3
If the value of “maxrepeat” is set to more than “3”, this is a finding.
Fix Text: Configure the operating system to require the change of the number of repeating consecutive characters when passwords are changed by setting the “maxrepeat” option.
Add the following line to “/etc/security/pwquality.conf conf” (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
maxrepeat = 3
Vul ID V-204414
Check Text: The “maxclassrepeat” option sets the maximum number of allowed same consecutive characters in the same class in the new password.
Check for the value of the “maxclassrepeat” option in “/etc/security/pwquality.conf” with the following command:
1
$ sudo grep maxclassrepeat /etc/security/pwquality.conf
maxclassrepeat = 4
If the value of “maxclassrepeat” is set to “0”, more than “4” or is commented out, this is a finding.
Fix Text: Configure the operating system to require the change of the number of repeating characters of the same character class when passwords are changed by setting the “maxclassrepeat” option.
Add the following line to “/etc/security/pwquality.conf” conf (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
maxclassrepeat = 4
Vul ID V-204415
Check Text: Verify the PAM system service is configured to store only encrypted representations of passwords. The strength of encryption that must be used to hash passwords for all accounts is SHA512.
Check that the system is configured to create SHA512 hashed passwords with the following command:
1
$ grep password /etc/pam.d/system-auth /etc/pam.d/password-auth
Outcome should look like following: /etc/pam.d/system-auth-ac:password sufficient pam_unix.so sha512 shadow try_first_pass use_authtok /etc/pam.d/password-auth:password sufficient pam_unix.so sha512 shadow try_first_pass use_authtok
If the “/etc/pam.d/system-auth” and “/etc/pam.d/password-auth” configuration files allow for password hashes other than SHA512 to be used, this is a finding.
Fix Text: Configure the operating system to store only SHA512 encrypted representations of passwords.
Add the following line in “/etc/pam.d/system-auth”: pam_unix.so sha512 shadow try_first_pass use_authtok
Add the following line in “/etc/pam.d/password-auth”: pam_unix.so sha512 shadow try_first_pass use_authtok
1
$ sudo vim /etc/pam.d/system-auth
1
$ sudo vim /etc/pam.d/password-auth
Note: Manual changes to the listed files may be overwritten by the “authconfig” program. The “authconfig” program should not be used to update the configurations listed in this requirement.
Vul ID V-204416
Check Text: Verify the system’s shadow file is configured to store only encrypted representations of passwords. The strength of encryption that must be used to hash passwords for all accounts is SHA512.
Check that the system is configured to create SHA512 hashed passwords with the following command:
1
$ grep -i encrypt /etc/login.defs
ENCRYPT_METHOD SHA512
If the “/etc/login.defs” configuration file does not exist or allows for password hashes other than SHA512 to be used, this is a finding.
Fix Text: Configure the operating system to store only SHA512 encrypted representations of passwords.
Add or update the following line in “/etc/login.defs”:
1
$ sudo vim /etc/login.defs
ENCRYPT_METHOD SHA512
Vul ID V-204417
Check Text: Verify the user and group account administration utilities are configured to store only encrypted representations of passwords. The strength of encryption that must be used to hash passwords for all accounts is “SHA512”.
Check that the system is configured to create “SHA512” hashed passwords with the following command:
1
$ grep -i sha512 /etc/libuser.conf
crypt_style = sha512
If the “crypt_style” variable is not set to “sha512”, is not in the defaults section, is commented out, or does not exist, this is a finding.
Fix Text: Configure the operating system to store only SHA512 encrypted representations of passwords.
Add or update the following line in “/etc/libuser.conf” in the [defaults] section:
1
$ sudo vim /etc/libuser.conf
crypt_style = sha512
Vul ID V-204418
Check Text: Verify the operating system enforces 24 hours/1 day as the minimum password lifetime for new user accounts.
Check for the value of “PASS_MIN_DAYS” in “/etc/login.defs” with the following command:
1
$ grep -i pass_min_days /etc/login.defs
PASS_MIN_DAYS 1
If the “PASS_MIN_DAYS” parameter value is not “1” or greater, or is commented out, this is a finding.
Fix Text: Configure the operating system to enforce 24 hours/1 day as the minimum password lifetime.
Add the following line in “/etc/login.defs” (or modify the line to have the required value):
1
$ sudo vim /etc/login.defs
PASS_MIN_DAYS 1
Vul ID V-204419
Check Text: Check whether the minimum time period between password changes for each user account is one day or greater.
1
$ sudo awk -F: '$4 < 1 {print $1 " " $4}' /etc/shadow
If any results are returned that are not associated with a system account, this is a finding.
Fix Text: Configure non-compliant accounts to enforce a 24 hours/1 day minimum password lifetime:
1
$ sudo chage -m 1 [user]

Vul ID V-204420
Check Text: If passwords are not being used for authentication, this is Not Applicable.
Verify the operating system enforces a 60-day maximum password lifetime restriction for new user accounts.
Check for the value of “PASS_MAX_DAYS” in “/etc/login.defs” with the following command:
1
$ grep -i pass_max_days /etc/login.defs
PASS_MAX_DAYS 60
If the “PASS_MAX_DAYS” parameter value is not 60 or less, or is commented out, this is a finding.
Fix Text: Configure the operating system to enforce a 60-day maximum password lifetime restriction.
Add the following line in “/etc/login.defs” (or modify the line to have the required value):
1
$ sudo vim /etc/login.defs
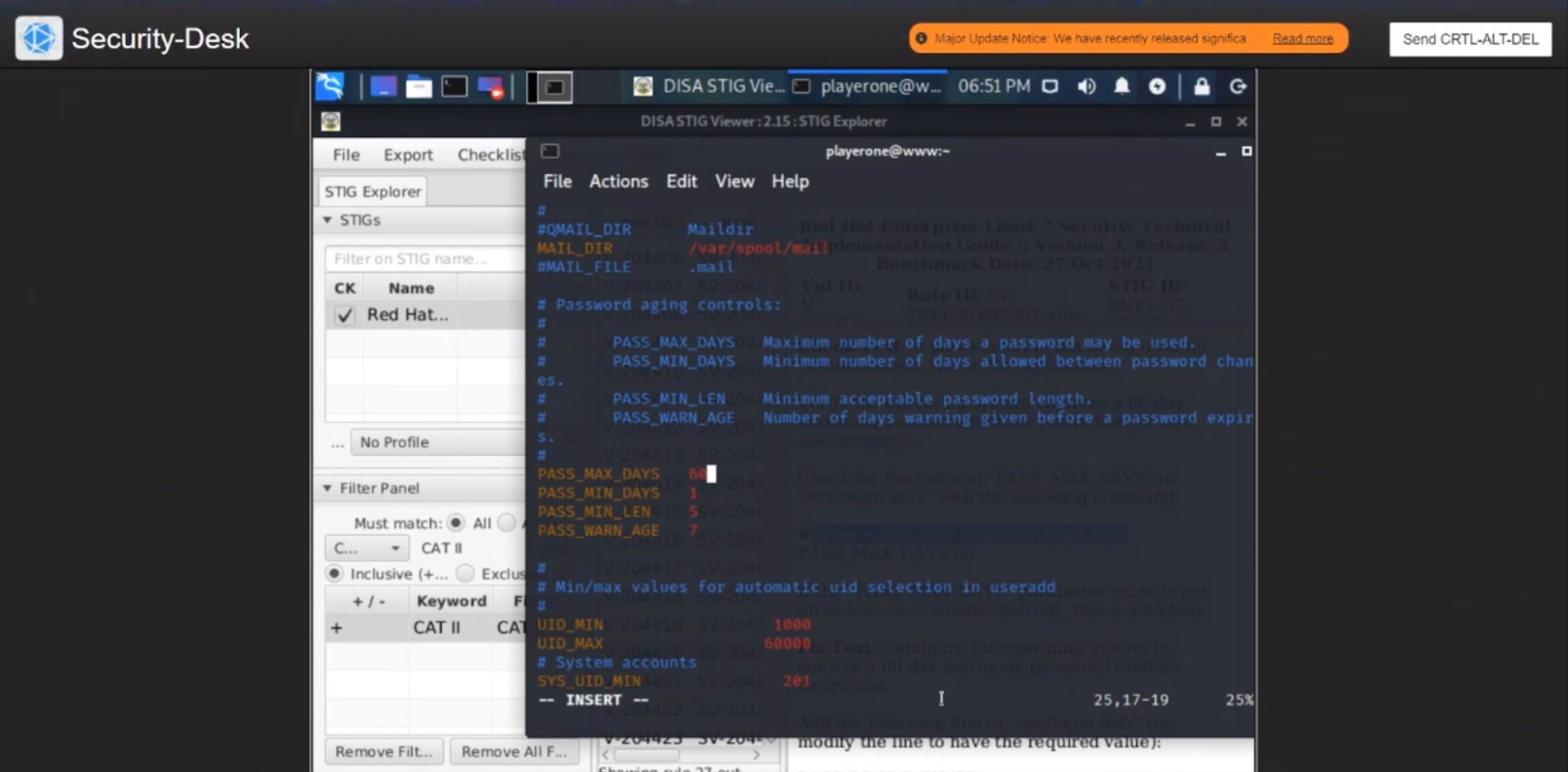
PASS_MAX_DAYS 60
Vul ID V-204421
Check Text: Check whether the maximum time period for existing passwords is restricted to 60 days.
1
$ sudo awk -F: '$5 > 60 {print $1 " " $5}' /etc/shadow
If any results are returned that are not associated with a system account, this is a finding.
Fix Text: Configure non-compliant accounts to enforce a 60-day maximum password lifetime restriction.
1
$ sudo chage -M 60 [user]

Vul ID V-204422
Check Text: Verify the operating system prohibits password reuse for a minimum of five generations.
Check for the value of the “remember” argument in “/etc/pam.d/system-auth” and “/etc/pam.d/password-auth” with the following command:
1
$ grep -i remember /etc/pam.d/system-auth /etc/pam.d/password-auth
password requisite pam_pwhistory.so use_authtok remember=5 retry=3
If the line containing the “pam_pwhistory.so” line does not have the “remember” module argument set, is commented out, or the value of the “remember” module argument is set to less than “5”, this is a finding.
Fix Text: Configure the operating system to prohibit password reuse for a minimum of five generations.
Add the following line in “/etc/pam.d/system-auth” and “/etc/pam.d/password-auth” (or modify the line to have the required value):
1
$ sudo vim /etc/pam.d/password-auth

password requisite pam_pwhistory.so use_authtok remember=5 retry=3
Note: Manual changes to the listed files may be overwritten by the “authconfig” program. The “authconfig” program should not be used to update the configurations listed in this requirement.
Vul ID V-204423
Check Text: Verify the operating system enforces a minimum 15-character password length. The “minlen” option sets the minimum number of characters in a new password.
Check for the value of the “minlen” option in “/etc/security/pwquality.conf” with the following command:
1
$ grep minlen /etc/security/pwquality.conf
minlen = 15
If the command does not return a “minlen” value of 15 or greater, this is a finding.
Fix Text: Configure operating system to enforce a minimum 15-character password length.
Add the following line to “/etc/security/pwquality.conf” (or modify the line to have the required value):
1
$ sudo vim /etc/security/pwquality.conf
minlen = 15
Vul ID V-204424
Check Text: To verify that null passwords cannot be used, run the following command:
1
$ grep nullok /etc/pam.d/system-auth /etc/pam.d/password-auth
If this produces any output, it may be possible to log on with accounts with empty passwords.
If null passwords can be used, this is a finding.
Fix Text: If an account is configured for password authentication but does not have an assigned password, it may be possible to log on to the account without authenticating.
Remove any instances of the “nullok” option in “/etc/pam.d/system-auth” and “/etc/pam.d/password-auth” to prevent logons with empty passwords.
1
$ sudo vim /etc/pam.d/system-auth
Note: Manual changes to the listed files may be overwritten by the “authconfig” program. The “authconfig” program should not be used to update the configurations listed in this requirement.
Vul ID V-204425
Check Text: To determine how the SSH daemon’s “PermitEmptyPasswords” option is set, run the following command:
1
$ grep -i PermitEmptyPasswords /etc/ssh/sshd_config
PermitEmptyPasswords no
If no line, a commented line, or a line indicating the value “no” is returned, the required value is set.
If the required value is not set, this is a finding.
Fix Text: To explicitly disallow remote logon from accounts with empty passwords, add or correct the following line in “/etc/ssh/sshd_config”:
1
$ sudo vim /etc/ssh/sshd_config
PermitEmptyPasswords no
The SSH service must be restarted for changes to take effect. Any accounts with empty passwords should be disabled immediately, and PAM configuration should prevent users from being able to assign themselves empty passwords.
Vul ID V-204426
Check Text: If passwords are not being used for authentication, this is Not Applicable.
Verify the operating system disables account identifiers (individuals, groups, roles, and devices) after the password expires with the following command:
1
$ grep -i inactive /etc/default/useradd
INACTIVE=35
If “INACTIVE” is set to “-1”, a value greater than “35”, is commented out, or is not defined, this is a finding.
Fix Text: Configure the operating system to disable account identifiers (individuals, groups, roles, and devices) 35 days after the password expires.
Add the following line to “/etc/default/useradd” (or modify the line to have the required value):
1
$ sudo vim /etc/default/useradd
INACTIVE=35
DoD recommendation is 35 days, but a lower value is acceptable. The value “-1” will disable this feature, and “0” will disable the account immediately after the password expires.
I completed my task by setting the rules according to U_RHEL_7_V3R6_STIG for the prod-web server as requested.

Each NICE Challenge has the following core elements: a narrative-driven scenario, a business environment (workspace), and a set of technical objectives and/or a written deliverable. Each of these elements is developed to immerse the player (student) in a real-world experience and create a valuable set of data allowing their curator (educator) to judge their readiness for the workforce.
About The NICE Challenge Project
